Protect Your Apps, AI, Workloads, Cloud, Agents Where It Matters: Runtime.
Detect and prevent security risks for every application you build, buy, and use.
Book a DemoTRUSTED BY
Shift where it matters - your running app
Get shift done




Shift left tools
Are point-in-time exercises
Surface theoretical vulnerabilities
Overwhelm developers
Are point-in-time exercises
Surface theoretical vulnerabilities
Overwhelm developers
CNAPP tools
Miss app-level attacks
Focus only on post-exploit activity
Overwhelm the SOC
Miss app-level attacks
Focus only on post-exploit activity
Overwhelm the SOC
KEY CAPABILITIES

Identify
All workloads, running apps, libraries, and more

Detect
Exploits and attacks across your apps and workloads


Prevent
Monitor application behavior at the library and function level
Platform
One platform.
Two solutions.
Three minutes to deploy.
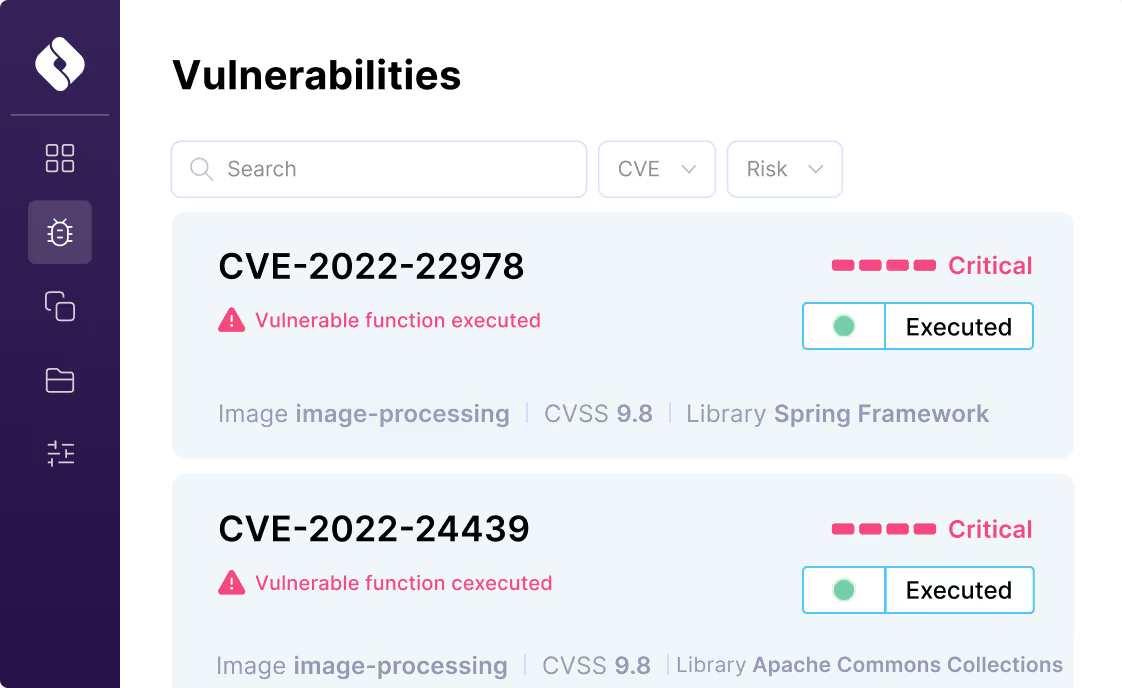
Runtime Vulnerability Management
Fix What Matters
Keep devs focused on features, not fixes. Unlike traditional left-side tools, Oligo detects which vulnerable libraries and functions are loaded and executed in the application – so your devs can stop wasting effort on non-exploitable findings.
Cloud Application Detection & Response
Stop Threats Fast
Uncover ongoing attacks – even from undisclosed zero-days. Unlike traditional right-side tools, Oligo sees each library in your application individually and detects when libraries are behaving in an irregular or insecure way.
the oligo spotlight


Vulnerabilities
Library status

Business Criticality

Internet Exposure

Data Access

High Privileges

Risk

Public Fix

Number of Results
270
/
270
Noise reduction
0
%
THE oligo sensor
Vision Beyond 20/20
Oligo’s technology is built on patented eBPF innovations, enabling unprecedented observability into application behavior at the library and function level with ultra-low (less than 1%) overhead. Oligo works on every application you use, develop, or buy — and deploys in minutes.
Use Cases
How Customers use Oligo
Know (and prove) which vulnerabilities expose you to real risks from every line of code in every application – not just open-source libraries.
Unmask attackers by spotting anomalous application behavior.

Rapidly generate VEX artifacts to satisfy compliance and customer requests.

Identify and stop attacks, even when they use unknown, undisclosed, or non-CVE “shadow” vulnerabilities.

Runtime Scanning Beyond SCA
Know (and prove) which vulnerabilities expose you to real risks from every line of code in every application – not just open-source libraries.

Real-Time Detection
Unmask attackers by spotting anomalous application behavior.

Automated Dynamic SBOM & VEX
Rapidly generate VEX artifacts to satisfy compliance and customer requests.

Zero-Day Prevention
Identify and stop attacks, even when they use unknown, undisclosed, or non-CVE “shadow” vulnerabilities.

Awards & Industry Recognition
Built to Defend Modern & Legacy apps
Oligo deploys in minutes for modern cloud apps built on K8s or older apps hosted on-prem.












































