No CompromisesSupply Chain Security
The only acceptable number of malicious packages in your applications: zero.
Solution Brief
.avif)
Block Malicious Package Attacks
Most vulnerabilities will never be exploited—but malicious packages start doing damage as soon as they find their way to your applications.
Oligo works differently from other supply chain security products, detecting behavioral anomalies at runtime and identifying malicious behavior in your code.
Protect Your Software
Supply Chain

See Every Application
See when libraries trigger unexpected or undesirable application behavior in every application you use, build, or buy.

Stop Attacks In Progress
If attackers activate malicious code that was previously dormant, the Oligo sensor will detect indicators of compromise and limit library-level permissions to prevent a breach.

Find Impacted Repos
After detection, Oligo can trace malicious code back to its original source repository so security patching can start fast.
Detect the “Undetectable”
Malicious code can be subtle and hard to identify—but with behavioral detection from Oligo, application malware has nowhere to hide.
Oligo can identify malicious code insertion regardless of their source, even when other tools fail.
.avif)
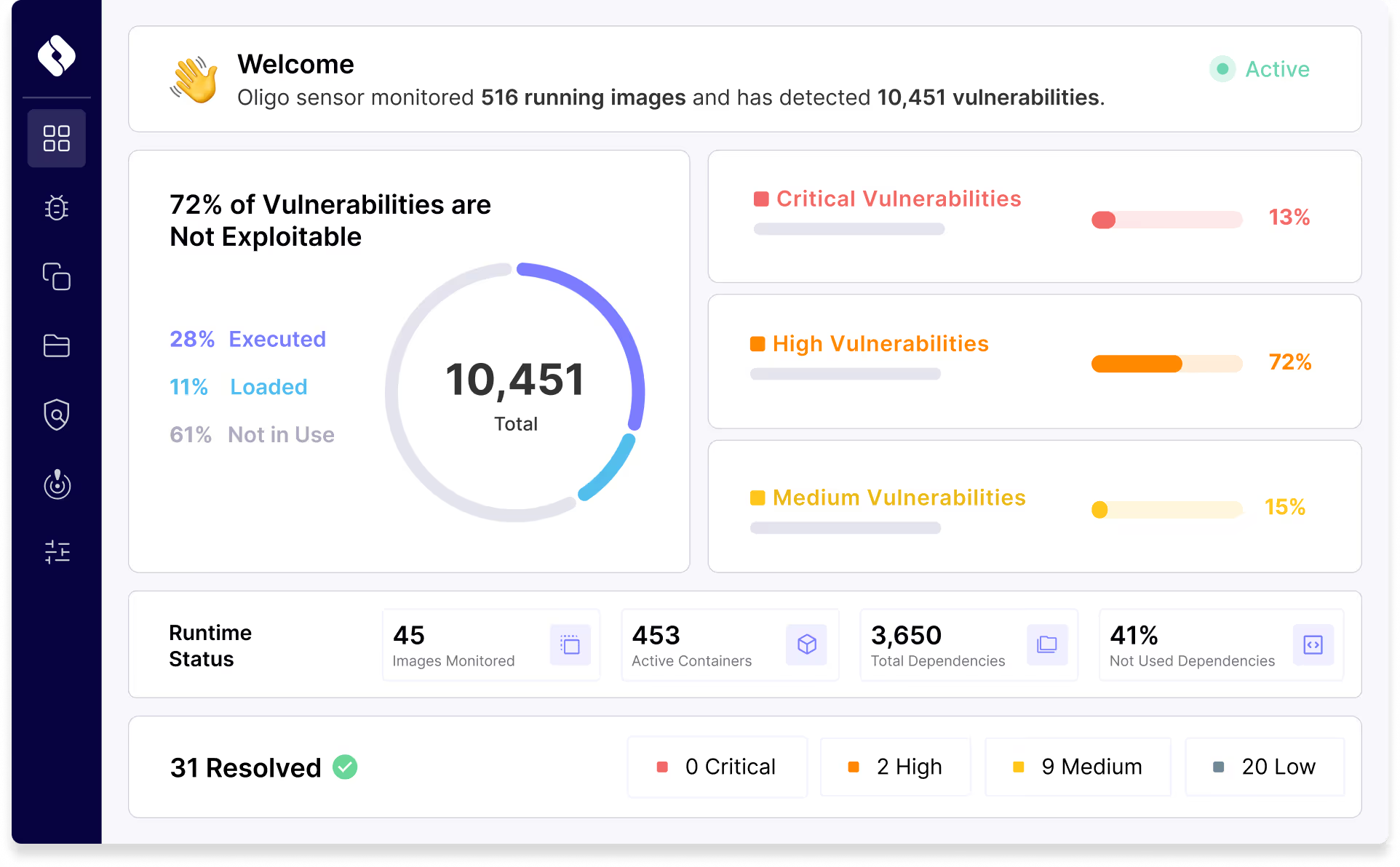
Fast, Complete Protection
Blocking malicious packages doesn’t have to be hard or time-consuming. Oligo takes minutes to deploy and makes no changes to your code.
Get total supply chain protection for all your applications—today.
Built to Defend Modern & Legacy apps
Oligo deploys in minutes for modern cloud apps built on K8s or older apps hosted on-prem.
