A recently discovered vulnerability could allow attackers to execute remote code on Linux systems that run the Common Unix Printing System (CUPS). This vulnerability chain enables arbitrary command execution with the privileges of the lp user. Though the exploit targets Linux systems, it can also affect macOS systems using CUPS.
TL;DR
- Attack vector: Wide Area Network (WAN) - also affects internet-facing servers
- Attack outcome: Remote code execution (RCE) with
lpuser privileges with some limitations inherited by the cupsd AppArmor profile - User interaction required: Yes (user needs to print something)
- CVE count: Four CVEs exploited for RCE
- Exposure: Thousands of CUPS services are exposed and vulnerable on the internet
- Vendor impact: Additional vendors under disclosure, beyond Linux
- CVEs involved:
- CVE-2024-47176
- CVE-2024-47076
- CVE-2024-47175
- CVE-2024-47177
CUPS Overview
CUPS is an open-source print management system for Unix-like operating systems. It enables computers to act as print servers, managing print jobs and queues. With its modular design, CUPS provides essential printing services and is commonly used on Linux desktops and macOS.
What is cups-browsed?
cups-browsed is a helper daemon within CUPS that is used to discover printers on the network and automatically configure them.
Where is CUPS used?
Using data from Censys, we found the following rough estimates for the number of exposed servers by CUPS version:
- CUPS/2.0: 23,000 servers
- CUPS/2.1: 5,000 servers
- CUPS/2.2: 5,000 servers
- CUPS/2.3: 12,000 servers
- CUPS/2.4: 18,000 servers
Vulnerability Overview
The vulnerability was initially reported to the maintainers on September 5th. On September 26th, 2024, EvilSocket (Simone Margaritelli) publicly disclosed the vulnerability (along with an RCE exploit) – in part because the vulnerability details had been leaked before the CVEs and patches were made available. Situations like this shine a spotlight on the importance of responsible disclosure and transparent response in order to minimize the impact that a vulnerability can have.
Here’s a breakdown of the attack, with the associated CVE numbers:
- Initial Access (CVE-2024-47176):
cups-browsed(<= 2.0.1) accepts unauthenticated requests on UDP port 631. Attackers send a crafted packet to trigger aGet-Printer-Attributesrequest to a malicious IPP server. - IPP Attribute Injection (CVE-2024-47076, CVE-2024-47175):
libcupsfiltersandlibppdfail to properly validate IPP attributes from a malicious server. This allows an attacker to inject malicious data into the CUPS system, creating a temporary PPD file. - Command Execution (CVE-2024-47177): The injected data contains a
FoomaticRIPCommandLinePPD parameter that instructs CUPS to execute thefoomatic-ripfilter. When a print job is sent, the attacker's command is executed.
Attack Flow
- The target machine is tricked riggered into connecting to a malicious IPP server.
- The server sends IPP attributes that inject a malicious PPD directive into a temporary file.
- A print job triggers the execution of the injected command.
Indicators of Compromise (IoCs)
These techniques have been used by the chain of vulnerabilities in this attack, based on the already-published POCs found online. Interestingly, the published POCs are identical to the POC in the original report, hinting that a leak happened during the disclosure process.
Behaviors observed:
- UDP requests to port 631
- followed by a new session
- Arbitrary command execution (creation of a new process) with user or group
lp- Command injection in
cups-filterswhen executingfoomatic-ripfilter, viacfGetPrinterAttributes5
- Command injection in
- Files created with user
lpall over the filesystemfind / -user lp -o -group lp 2>/dev/null
- cupsFilter2 Foomatic-rip filter was used in to create the file.
Files used in the public POCs:
- If you have a vulnerable server that is exposed to the internet, check for the existence of any of these files:
/tmp/PWNED/tmp/I_AM_VULNERABLE
- If they exist, assume some exploited your infrastructure successfully. It means that the public POC was carried successfully against your infrastructure and someone is aware of that.
Mitigation and Remediation
Am I vulnerable?
To check if a vulnerable service is installed:
systemctl status cups-browsedsystemctl status cups
To check if port 631 is in use:
sudo netstat -ant | grep ":631"sudo lsof -i UDP:631
If any of the commands above indicate there is no running service, you are not vulnerable to these CVEs.
How Do I Fix This?
CUPS isn’t installed by default on all Linux distributions, but it is often included on desktop distributions like Ubuntu Desktop or Debian 8/9. Server distributions usually don’t have it installed, but it depends on the Linux distribution and version.
If you have cups-browsed running in your environment, we recommend the following:
- If your machine is not used for printing: Disable and remove
cups-browsed(see below) - If you only use the printer for printing locally, but still need printer auto-discovery in your network: Upgrade to the latest versions of CUPS - specifically
cups-browsed. You can also disable cups-browsed (see below). - If you are printing over the WAN (public internet):
- Upgrade CUPS to the latest version
- Disable the
cups-browsedservice - Add access control and firewall rules to port 631 (UDP) (see below)
- Consider managing the IP addresses explicitly, so you could control the IPs that can trigger a printing job, making sure they are authorized.
Fix Details
- Removing CUPS
- Stop The Service:
sudo systemctl stop cups
- Disable the service:
sudo systemctl disable cups
- Uninstall the service:
sudo apt purge cups
- Stop The Service:
- Adding Firewall Rules: The following commands will cover most linux distributions, and will block access to the port that CUPS uses:
- If you use
iptables:sudo iptables -A INPUT -p tcp --dport 631 -j DROPsudo iptables -A INPUT -p udp --dport 631 -j DROP
- If your Linux uses
ufw:sudo ufw deny 631/tcpsudo ufw deny 631/udp
- If you use
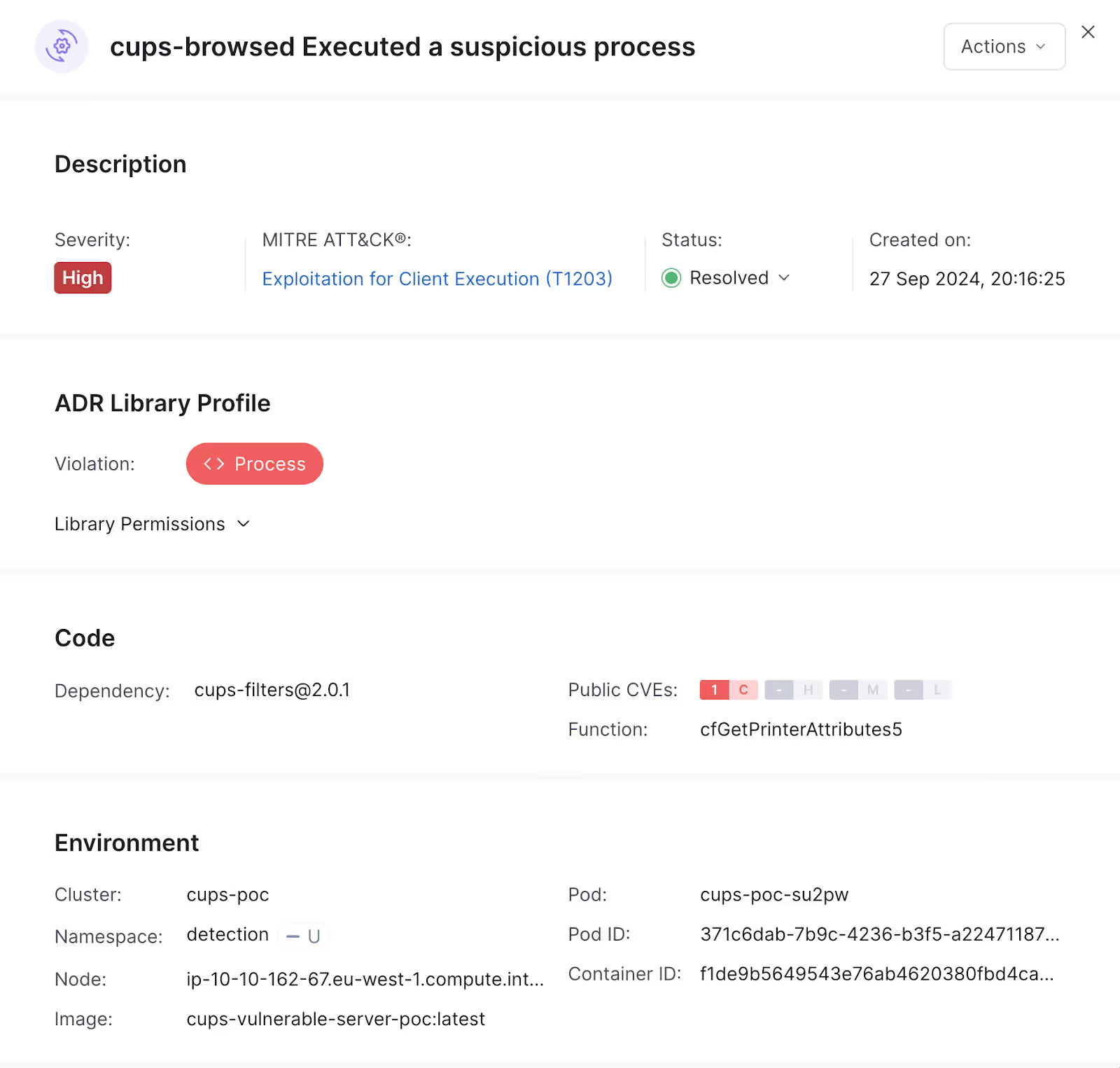
How Oligo Can Help Detect the Attack
At Oligo, our Application Detection and Response (ADR) technology provides a unique approach to detecting vulnerabilities such as those exploited in this CUPS RCE attack. Oligo ADR analyzes the stacks and behaviors of programs to identify anomalies.
Because Oligo collects behavioral data from multiple parts of the application, our ADR is able to detect changes in program execution flows caused by command injection attacks. Typically, logical vulnerabilities (i.e., not memory related heap/stack overflows etc) present a challenge for modern approaches as they do not directly change the ‘code flow’ (stack/ behavior/ stack trace, etc.) – demonstrating how pivotal it is to collect and analyze data from multiple parts of applications.

References:
- https://www.evilsocket.net/2024/09/26/Attacking-UNIX-systems-via-CUPS-Part-I/
- https://bugzilla.redhat.com/show_bug.cgi?id=2314289
- https://github.com/OpenPrinting/libcupsfilters/security/advisories/GHSA-w63j-6g73-wmg5
- https://www.cups.org/
- https://www.cve.org/CVERecord?id=CVE-2024-47177
- https://www.cve.org/CVERecord?id=CVE-2024-47176
- https://www.cve.org/CVERecord?id=CVE-2024-47175
- https://www.cve.org/CVERecord?id=CVE-2024-47076






