What is Application Detection & Response (ADR)?
Application Detection & Response (ADR) is a security solution that uses application-layer insights to identify indicators of compromise and mitigate malicious activity in real time. ADR focuses on the application layer itself at runtime, whereas other approaches focus exclusively on perimeter of the application at the infrastructure or the network layers.
ADR solutions detect when application components behave in anomalous ways that indicate the very beginning of an attack, allowing security teams to stop attacks immediately before they escalate. ADR uses modern, non-intrusive observability method that is designed to be lightweight so that it does not impact application performance or stability, making it distinct from older runtime approaches, such as Runtime Application Self Protection (RASP). In addition, ADR provides application-level analysis to security teams without needing access to source code, or requiring instrumentation to the application beforehand by developers.
Because ADR operates just below the operating system layer, it can provide deep insights into attacks regardless of the runtime infrastructure–cloud, virtual machine, or bare-metal server.
What challenges does ADR solve?
Application blindspots
Application attacks are on the rise, and attackers know if they can exploit vulnerabilities at the application level they can remain undetected for a long time, covering their tracks as they go. "Shift-left" solutions like Software Composition Analysis (SCA) and Static Application Security Testing (SAST) are not enough—they can help developers make applications more secure before they deploy, but many vulnerabilities will still slip through the cracks.
Most cyberattacks target applications, but most detection and response solutions, including Web Application Firewalls (WAF) and Cloud Workload Protection Platforms (CWPP) , don’t protect the core application itself - instead they protect the hosting infrastructure or perimeter of the application. With this blindspot, organizations can only detect attacks once they’ve already successfully gained a foothold within the application infrastructure –meaning they have little insight as to how they were compromised in the first place.
Detection delays
The average time it took organizations to identify a breach in 2024 was 204 days according to IBM. Breaches are costly, each one costing on average over $4 million, and the longer they take to detect, the more that dollar amount rises. For critical applications, even one day is too long. Security practitioners need tools that help them identify application attacks within seconds, not days.
Response precision
If a detection tool sees an application as a black box, what is the next step when an attack is detected? More often than not, all that can be done is to take the application down while the attack vector is identified and closed, or try to eradicate the attacker as fast as possible to minimize damage. This sledgehammer approach leads to unnecessary downtime. For many organizations, significant downtime of a critical application could rival the cost of a breach. Finally, this approach addresses the symptoms (post-exploit behavior) rather than the cause (initial exploits).
How Application Detection and Response Works
ADR operates by combining comprehensive application insights with real-time monitoring and automation.
Application Monitoring
Application monitoring involves the continuous observation of an application’s behavior to ensure security and reliability. ADR solutions achieve this by embedding lightweight sensors where each application is deployed or by using open source telemetry data to track real-time data flows, code execution, and user activity.
This granular monitoring helps identify unusual application behaviors, such as unexpected crashes or excessive resource usage, that might indicate a potential security threat. By gathering detailed runtime context, ADR tools pinpoint vulnerabilities and detect attack patterns that traditional monitoring systems miss.
Profiling of Open-Source Libraries
Many modern applications rely heavily on open-source libraries. ADR solutions mitigate risks associated with these dependencies by profiling the normal behavior of these libraries during routine operations. By establishing a baseline, any deviation—such as unauthorized changes or abnormal function calls—can signal a potential compromise, such as a supply chain attack.
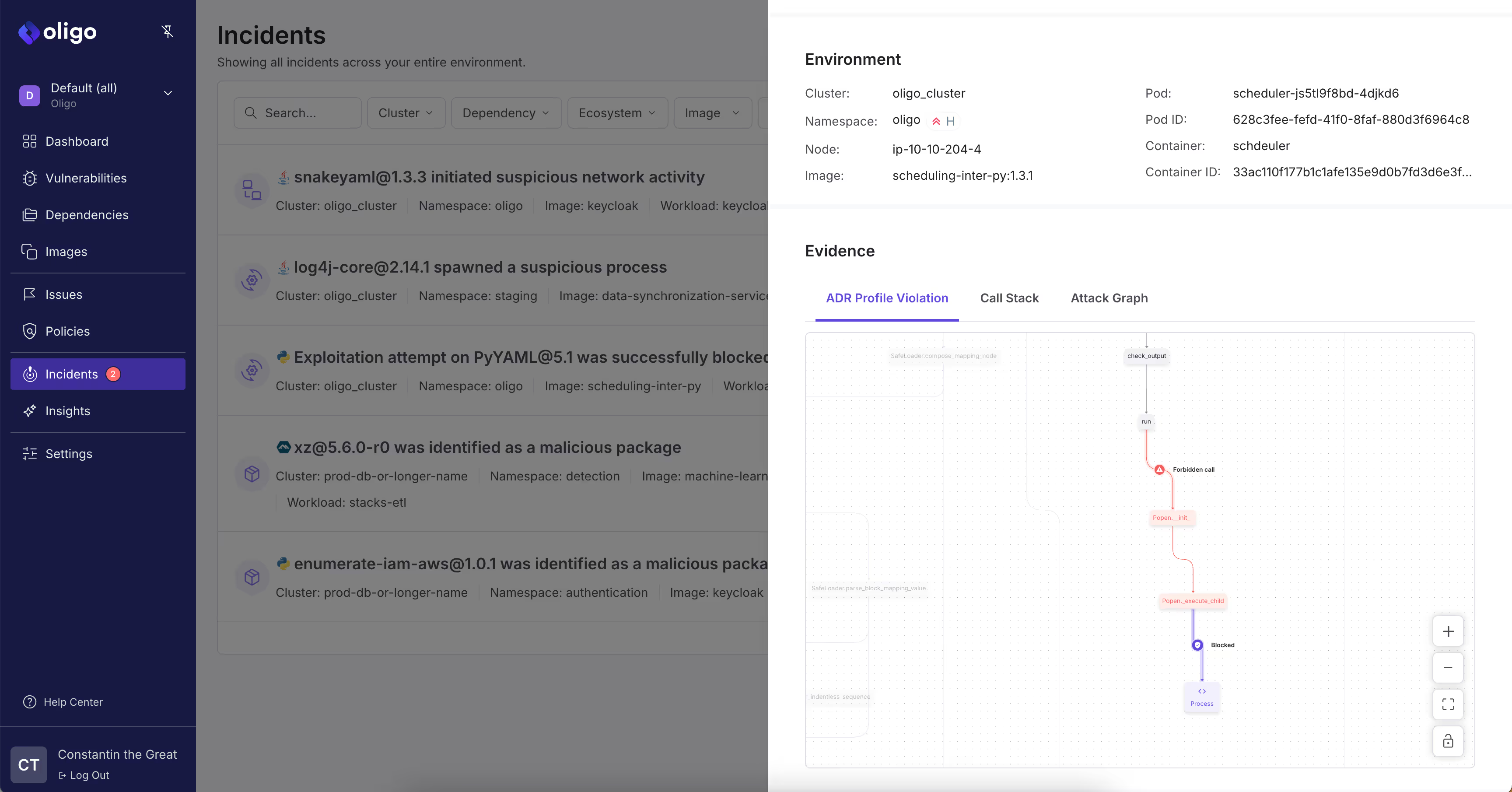
For example, PyYaml, a library used to deserialize data - should not perform code execution on the host level. ADR detects when libraries deviate from their normal behavior and generate an alert - even when there isn’t a known vulnerability with a given library.
This capability is especially important given the prevalence of attacks that exploit vulnerabilities in third-party components. By identifying irregularities early, ADR can prevent attackers from injecting malicious code into application environments.
Anomaly Detection
ADR utilizes advanced behavioral analysis and machine learning (ML) to detect anomalies. By analyzing runtime data, ADR tools recognize deviations from normal application behavior. For instance, a library that is known for logging events may suddenly try to perform remote code execution.
These anomalies are flagged for further evaluation, ensuring that potential threats are identified promptly without overwhelming security teams with false positives.
Threat Analysis and Alerting
Once a potential threat is identified, ADR systems conduct in-depth analysis to assess its severity and impact. This process involves correlating anomalies with known attack signatures and vulnerabilities, providing context to understand the scope of the attack.
The results are distilled into actionable alerts that prioritize critical threats, enabling security teams to respond quickly. By presenting clear insights into attacks, ADR reduces the time and effort required for investigation and remediation.
Automated Response
Advanced ADR solutions go a step further by implementing automated response mechanisms. These systems can block malicious actors by isolating and blocking malicious functions of code, while keeping the rest of the application intact - all without waiting for manual intervention. Automated responses reduce response times significantly, helping to mitigate the impact of an attack before it spreads.
For instance, if a function is trying to perform a malicious action, the ADR tool can immediately reject it without having to kill or quarantine containers, VMs, or any infrastructure that is associated with the application.This ensures that the application remains operational while eliminating the exploit outright. These capabilities make ADR a valuable asset for securing critical applications in real time.
Key benefits and capabilities of ADR
- Immediate detection - ADR enables security teams to be alerted the instant a library is used in an unusual way, indicating compromise. This brings the dwell time (the amount of time between an attacker gaining access and the attacker being detected) of application-layer attacks down to mere seconds.
- Exploit prevention- Knowing exactly which component is trying to perform which malicious action allows security teams to use dynamic, flexible rules to block malicious behavior at the function level without compromising the rest of the application.
- Context and visibility - ADR is able to provide key insights, including the specific library function involved in an attack, to help security teams and developers focus their patching efforts.
- Attack vector agnostic - An ADR solution doesn't care if the attack comes via a known CVE, zero-day vulnerability, or misconfiguration.
- Simple deployment - A tool that takes an entire team to set up and maintain has limited value. An ADR solution uses lightweight agents, is easy to deploy, and starts defending applications immediately.
{{expert-tip}}
Common Use Cases of Application Detection and Response
Detecting and Responding to Application Security Risks
ADR solutions can identify and address unusual activity at the application layer, as well as known attack behavior (i.e. OWASP Top 10 risks). By embedding advanced monitoring capabilities, ADR can detect anomalies such as supply chain attacks, malicious code injection, fileless attacks, dependency hijacking, and other exploits.
Detecting suspicious workload behavior
In addition to suspicious code behavior, ADR tools flag suspicious behavior at the workload level that may indicate a breach has already taken place. This includes privilege escalation, malware, lateral movement attempts, and more. These anomalies are logged and correlated alongside to initial exploits to give incident responders a full view of attacks, enabling swift investigation and remediation before significant damage occurs.
Preventing Exploitation of Zero-Day Vulnerabilities
ADR excels at protecting applications from zero-day vulnerabilities in both custom and third-party code. These attack vectors, unknown to the public and without available patches, pose a significant risk because traditional application security tools typically look for known vulnerabilities.
Using behavioral profiling, ADR establishes baselines for normal application activity, including that of open-source components. Deviations from these baselines can indicate a novel supply chain attack or a newly exploited zero-day vulnerability. This proactive monitoring enables security teams to detect, report, and mitigate such threats before they can cause widespread harm.
Securing Software Supply Chains
Applications often rely on third-party libraries, APIs, and other external dependencies, which can introduce vulnerabilities. ADR ensures the integrity of these components by monitoring their behavior in real time. For instance, ADR can flag unauthorized function calls stemming from a library or detect unexpected call stacks. These insights allow security teams to intervene quickly, preventing potential compromises within the supply chain.
By continuously profiling third-party components, ADR detects deviations from expected behavior, signaling possible supply chain attacks. This proactive monitoring helps mitigate risks posed by compromised dependencies, ensuring a secure foundation for application functionality.
Securing GenAI
The majority of GenAI usage stems from embedded, open source frameworks (such as Meta Llama). ADR can identify all usage of GenAI in first party apps, profile libraries within open source frameworks, and validate and control model output of AI systems. In fact, many of the OWASP top 10 risks for large language model applications can be detected by ADR solutions.
Enhancing Compliance and Audit Processes
ADR simplifies compliance by maintaining detailed logs of application activity, vulnerabilities, and security responses. These records provide a transparent view of how security measures are applied, making it easier to meet regulatory requirements and pass audits. For example, ADR tools can show a clear history of detected threats and remedial actions, ensuring accountability.
In addition to compliance, these logs support continuous improvement by highlighting trends in vulnerabilities and attack patterns. This allows organizations to refine security practices, align with industry standards, and avoid penalties related to non-compliance.
Application Detection and Response vs. Other Security Measures
ADR exists to solve the "first mile problem" of runtime security: what is happening within the applications themselves when they’re deployed to production. ADR solves a gap that can’t be covered with other technologies, while providing the same functionality found in container security and cloud workload protection platforms (CWPP).
What is the difference between ADR and RASP?
Runtime Application Self Protection (RASP) was an early attempt at gaining security insights from applications, but has largely been ignored by security practitioners. RASP requires developers to build it into each application and set rules for application logic, which makes utilizing RASP costly and difficult to scale. RASP also suffers from reliability and performance issues, directly impacting application uptime and availability.
In contrast, ADR does not need to be deployed prior to the development of an application and can detect signs of compromise in third party applications as well. ADR solutions introduce minimal impact to applications since they are deployed alongside each node or machine where the application is hosted.
What is the difference between ADR and WAF?
A Web Application Firewall (WAF) protects applications from known malicious traffic. Like ADR, WAF can protect applications regardless of where they are hosted, but unlike ADR, WAF can often be bypassed by clever attackers and is limited in insights about attacks as it has no visibility into applications.
What is the difference between ADR and CSPM?
Cloud Security Posture Management (CSPM) solutions scan the infrastructure layer and are concerned with managing configurations and compliance settings. CSPM can detect certain kinds of vulnerabilities that can lead to attacks, but does not detect active threats at the application layer.
What is the difference between ADR and CNAPP/CWPP?
A Cloud Workload Protection Platform (CWPP) is focused on suspicious events, misconfigurations, and malware detection. Cloud Native Application Protection Platform (CNAPP) combines CWPP and features with posture management and detection and response capabilities. CNAPP and CWPP both protect at the perimeter, leaving them without the application-level visibility that ADR offers.
What is the difference between ADR and DAST?
Dynamic Application Security Testing (DAST) solutions identify vulnerabilities in running applications by simulation real-world attacks against known vulnerabilities and risks. They can help mitigate risks, but they are point-in-time exercises. ADR offers continuous protection against both known and unknown attacks, providing more comprehensive security.
Oligo ADR
Oligo ADR is the only fully featured ADR on the market today. Our approach to ADR puts customer needs first:
- Low overhead - The Oligo Sensor is lightweight with a technical overhead of less than 1%.
- Easy deployment - Oligo ADR takes minutes to deploy and begins protecting immediately.
- Fast-acting detection - Oligo ADR can bring the time for detecting an application breach down from six months to under 1 second.
- First and third-party applications - Oligo ADR works on all the applications you build, buy, or use—and can tie findings back to specific software components, even without access to source code.
- Portability - On-prem or off, VMs or containers, private or public cloud – Oligo ADR protects applications however they're hosted.
- Non-intrusive instrumentation - Oligo ADR sits at the operating system layer and uses patented eBPF technology to gain application insights without getting in the way of development.
See Oligo ADR in Action
Book a live demo to see how Oligo ADR identifies exploitation in all your applications, using library-level behavioral profiles to identify anomalous behavior and unmask application-layer attacks in real-time.
Read more:
ADR - The Future of Runtime - James Berthoty from Latio Tech highlights the shift from EDR to ADR, emphasizing the limitations of traditional EDR in containerized environments and ADR's comprehensive visibility across cloud, container, and application contexts.
How ADRs solve the the last mile problem of application security - Mouad Kondah from Deep Kondah explains how ADRs address application security challenges by providing real-time monitoring and response, surpassing the limitations of traditional EDR and RASP solutions.
Oligo ADR Prevents LLM Prompt Injection - Prompt injection can lead LLMs to produce harmful outputs or execute malicious code. Oligo ADR detects and stops these threats instantly.
Oligo ADR Mitigates PaddlePaddle Shadow Vulnerability - PaddlePaddle, a popular deep learning platform, has a critical shadow vulnerability in its Paddle Serving component. Oligo ADR detects and neutralizes this threat.

.png)


.png)