TL;DR
Deep learning and AI infrastructure are prime targets for attackers, especially as they utilize valuable data for training models. PaddlePaddle, a popular DL platform, has a critical shadow (no CVE) vulnerability in its Paddle Serving component, making it susceptible to remote code execution. Oligo ADR effectively detects and mitigates this threat.
Introduction
PaddlePaddle is a Chinese open-source DL platform, similar to other popular AI frameworks like Google's TensorFlow and Facebook's PyTorch. Paddle Serving relies on the deep learning framework PaddlePaddle, aiming to help deep learning developers easily deploy online prediction services.
It consists of 2 frameworks:
- High-performance C++ Serving.
- Highly easy-to-use Python Pipeline.
PaddlePaddle Serving Shadow Vulnerability
The NumPy.load function of the popular NumPy library loads arrays or pickled objects from .npy, .npz or pickled files. On CVE-2019-6446 it turned out that NumPy allows Pickle unsafe loading by default, which allows remote attackers to achieve remote code execution via a crafted serialized object. The fix for CVE-2019-6446 was to set the NumPy.load allow_pickle argument to False by default. However, Pickle loading is still possible with the NumPy.load function when the developer sets allow_pickle to True. Therefore, the responsibility for using it securely moves to the developer, as stated as NumPy’s docs.
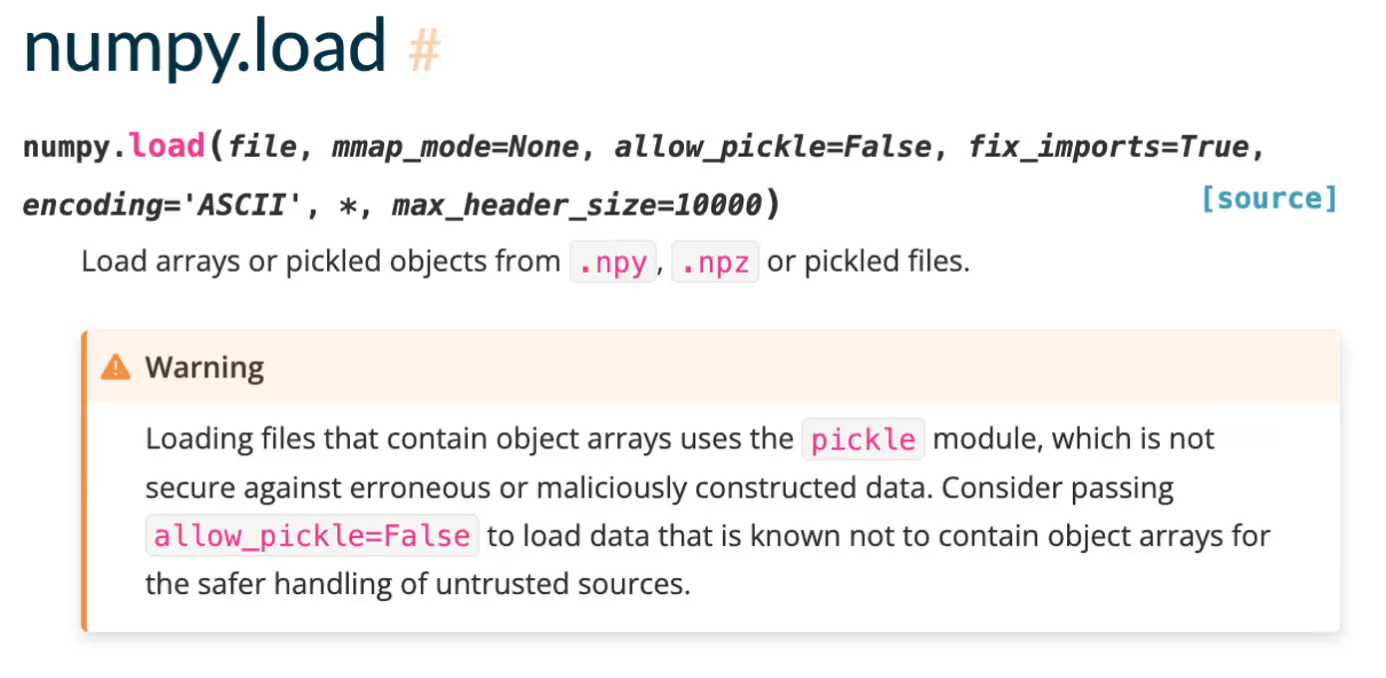
Unfortunately, the Python Pipeline component of Paddle Serving uses NumPy.load function with this unsafe argument, enabling the loading of Pickle objects and thus Remote Code Execution.
def proto_tensor_2_numpy(self, tensor):
""" Convert proto tensor to numpy array, The supported types are as follows: Args: tensor: one tensor in request.tensors.
Returns: np_data: np.nd
numpy, the tensor data is converted to numpy. lod_info: np.ndnumpy, lod info of the tensor data, None default. """
......
if tensor.elem_type == 0: # VarType: INT64
np_data = np.array(tensor.int64_data).astype(int64).reshape(dims)
elif tensor.elem_type == 1: # VarType: FP32
np_data = np.array(tensor.float_data).astype(float32).reshape(dims) ......
elif tensor.elem_type == 13: # VarType: BYTES
byte_data = BytesIO(tensor.byte_data)
np_data = np.load(byte_data, allow_pickle=True)From PaddleServing Code Source
By controlling the tensor argument of proto_tensor_2_numpy, an attacker can provide a malicious Pickle and gain Remote Code Execution on Paddle Serving server.
What is Shadow vulnerability and why is it significant?
Shadow vulnerabilities are a type of security flaw that we identified in many open-source libraries. These vulnerabilities do not have a CVE assigned to them, and they often marked as 'no-fix' by the maintainers of the library, leading to what we refer to as 'vulnerable-by-design' scenarios. This is exactly what we discovered in the use of NumPy within the Paddle Serving code.
For instance, NumPy version 1.21.6 does not have an assigned CVE, despite allowing Remote Code Execution when used with an insecure argument. This lack of formal recognition means traditional security tools like SCAs cannot detect these issues, making them particularly dangerous. Paddle Serving Server is widely used to deploy PaddlePaddle models and projects. As such, any server utilizing Paddle Serving is susceptible to RCE, even with the latest version (v0.9.0 at the time of writing). This underscores the critical nature of addressing shadow vulnerabilities through advanced detection methods like Oligo ADR.
How Does Oligo ADR Detect the Exploitation of this Shadow Vulnerability?
While SCA fail to identify shadow vulnerabilities like the one in NumPy used by Paddle Serving, real-time detection is essential for identifying and mitigating these threats at the moment they are exploited.
Oligo ADR addresses this gap by maintaining an extensive and constantly updated database of runtime profiles for numerous third-party libraries. The Oligo platform leverages these profiles to identify unusual library behavior, signaling the initiation or progression of an exploit.
For the NumPy library, Oligo’s prebuilt profiles have never recorded legitimate instances of code execution within the Pickle processing flow. Consequently, Oligo swiftly flags any attempt to trigger injection exploits, automatically generating an incident report in the Oligo ADR platform, even in the absence of a CVE related to the NumPy library.
Exploitation and Detection using Oligo ADR
In this example, we will deploy the PaddleOCR model with the Paddle Serving Server to demonstrate the exploitation. Other PaddlePaddle official projects that were deployed through Paddle Serving were tested and found to be vulnerable, for example - PaddleVideo, the UCI prediction model, and more.
PaddleOCR is an advanced OCR (technology that enables machines to recognize and extract text from images) toolkit based on deep learning, performing text detection and recognition tasks. PaddleOCR was created by PaddlePaddle.
One of the recommended deployment methods (according to the PaddleOCR project documentation) is the Paddle Serving Server.

In order to exploit the vulnerability, one just need to send a prediction request to the server using the following malicious payload:
data = {
"key": ["image"], "value": [image],
"tensors":
[
{
"name": ":psyduck:",
"elem_type": 13,
"byte_data": "MALICIOUS_PICKLE" }
] }The malicious Pickle attached to the prediction request
The byte_data is a Pickle that contains the malicious command that will be executed once the NumPy loading occurs.
Oligo ADR represents an instant way to identify and stop exploitation of this shadow vulnerability. As the only product on the market capable of detecting and responding to both known and unknown threats in application components, Oligo ADR has given security teams a new way to see intrusions instantly—and block them before they become major breaches.

.png)


.png)